Appearance
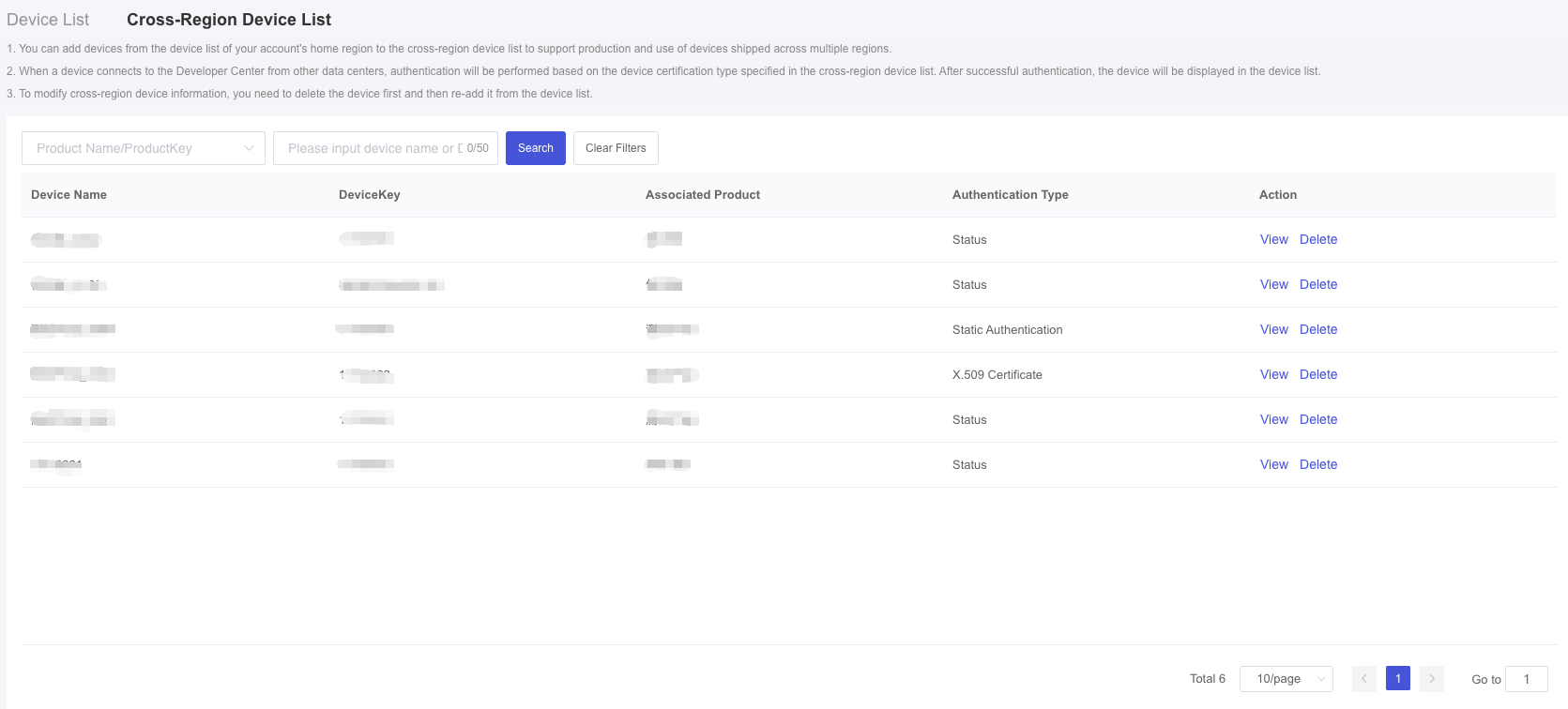
Cross-Region Device List
This section introduces device actions in "Device Maintenance".
Prerequisites
A product has been created.
Steps
- Log in to Develop Center, click "Device Management" → "Device Maintenance" in the left-hand navigation bar to enter the "Cross-region device list" within the account registration's region.
When your device has cross-region usage scenarios, you can add it from the device list to the cross-region device list.
After adding it, you do not need to re-add the device in other data centers. When the device connects and logs in to a data center it has never accessed before, the platform will verify it using the information from the cross-region device list. Once verified, basic device information (such as DS and SN) will be automatically synchronized to the data center where the connection occurs, ensuring data consistency across all regions.
To modify cross-region device information, you need to delete the device first and then re-add it from the device list.